Description
Turns your phone into a network camera with multiple viewing options. View your camera on any platform with VLC player or web browser. Stream video inside WiFi network without internet access.
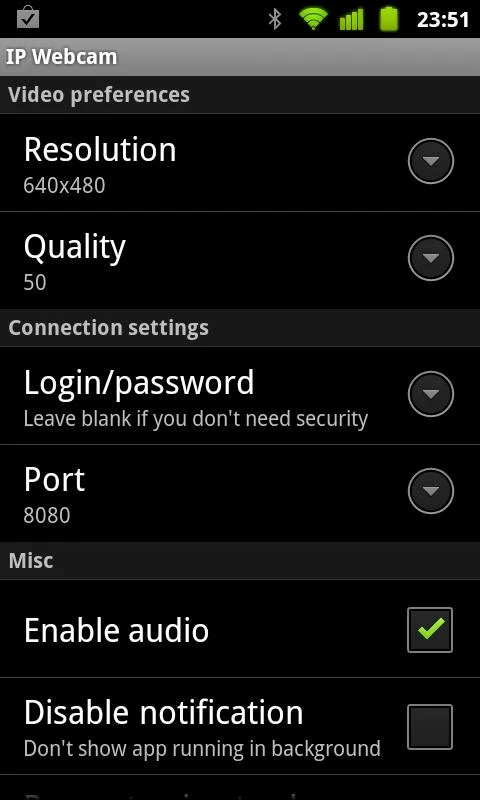
Use IP Webcam with tinyCam Monitor on another android device or with third-party MJPG software, including video surveillance software, security monitors and most audio players.
Video chat support (e.g. Skype, Chat roulette, only video stream for Windows only via an universal MJPG video streaming driver)
Email me if you have questions after reading the FAQ.
THINGS U NEED
..android phone above 2.3
..computer or laptop (laptop recommended)
..wifi router of one more phone to make wifi hot spot
step-1
download ip webcam app on your android
step-2
now start ip webcam app on your phone, your camera will also open select start server (option).it will give a assigned ip address to your phone by wifi router or hotspot whatever you are using
step -3
open web browser chrome is the best it has in built flash player helps in stream videos from the phone enter the assigned ip in the new tab a menu will appear select the broadcast option which is the 5 option .. and its done
..android phone above 2.3
..computer or laptop (laptop recommended)
..wifi router of one more phone to make wifi hot spot
step-1
download ip webcam app on your android
step-2
now start ip webcam app on your phone, your camera will also open select start server (option).it will give a assigned ip address to your phone by wifi router or hotspot whatever you are using
step -3
open web browser chrome is the best it has in built flash player helps in stream videos from the phone enter the assigned ip in the new tab a menu will appear select the broadcast option which is the 5 option .. and its done
NOTE
ALL YOUR DEVICES PC LAPTOP OR PHONE WILL BE CONNECTED TO SAME WIFI ROUTER
DONT HAVE WIFI USE WIFI HOTSPOT FROM ANOTHER PHONE AND THE BEST THING NO NEED OF INTERNET CONNECTION USE WIFI JUST LIKE BLUE TOOTH...
enjoy....comment if didn't understand ..
ALL YOUR DEVICES PC LAPTOP OR PHONE WILL BE CONNECTED TO SAME WIFI ROUTER
DONT HAVE WIFI USE WIFI HOTSPOT FROM ANOTHER PHONE AND THE BEST THING NO NEED OF INTERNET CONNECTION USE WIFI JUST LIKE BLUE TOOTH...
enjoy....comment if didn't understand ..